FEATURE SPOTLIGHT – DEVICE CONTROL
An almost universal feature of every endpoint is the ability to plug in USBs and other peripheral devices. Businesses need that flexibility, but plug-in devices introduce a vulnerability to enterprise security. Whether it’s a poisoned device containing malware, or simply a route for disgruntled employees to steal and distribute company data, external devices are essentially a blind spot for the enterprise.
We are delighted to announce the addition of Device Control to our platform. SentinelOne Device Control gives you the capability to manage the use of USB and other peripheral devices across your entire network, all from the convenience of your SentinelOne Management Console.
Use is declining, but USBs are not going away
While it’s true that cloud services have taken over much of the heavy lifting regarding data storage and transfer in the enterprise, USBs are still an essential business tool. Millions of these devices are still produced and distributed annually. They may be destined for use in homes or businesses, given away at trade shows for marketing purposes, or used to make file transfers when connectivity is either down or impractical for some reason.

Given their continuing ubiquity, it makes sense to employ device control for several reasons:
- Visibility: Administrators may want to create an inventory of all peripheral devices on the network. You cannot protect what you cannot see.
- Enterprise Data Loss Prevention: Managing device access both on and off the network means you can block the unauthorized transfer of data through USBs and other peripherals.
- Malware Prevention: a USB can be a lethal weapon – Stuxnet was deployed that way. During Black Hat 2016, a group of researchers experimented throwing USBs in the parking lots. 98% were picked up and 45% were able to phone home after being inserted into a device. Encryption and disabling AutoRun are insufficient.
- Compliance: Administrators may want to prevent users from connecting any peripheral device, but still allow some to work without interruption (such as input devices like mouse, keyboard, etc). Device Control can allow users to connect only peripheral devices that are on an “approved” list.
Set your Policy with Ease
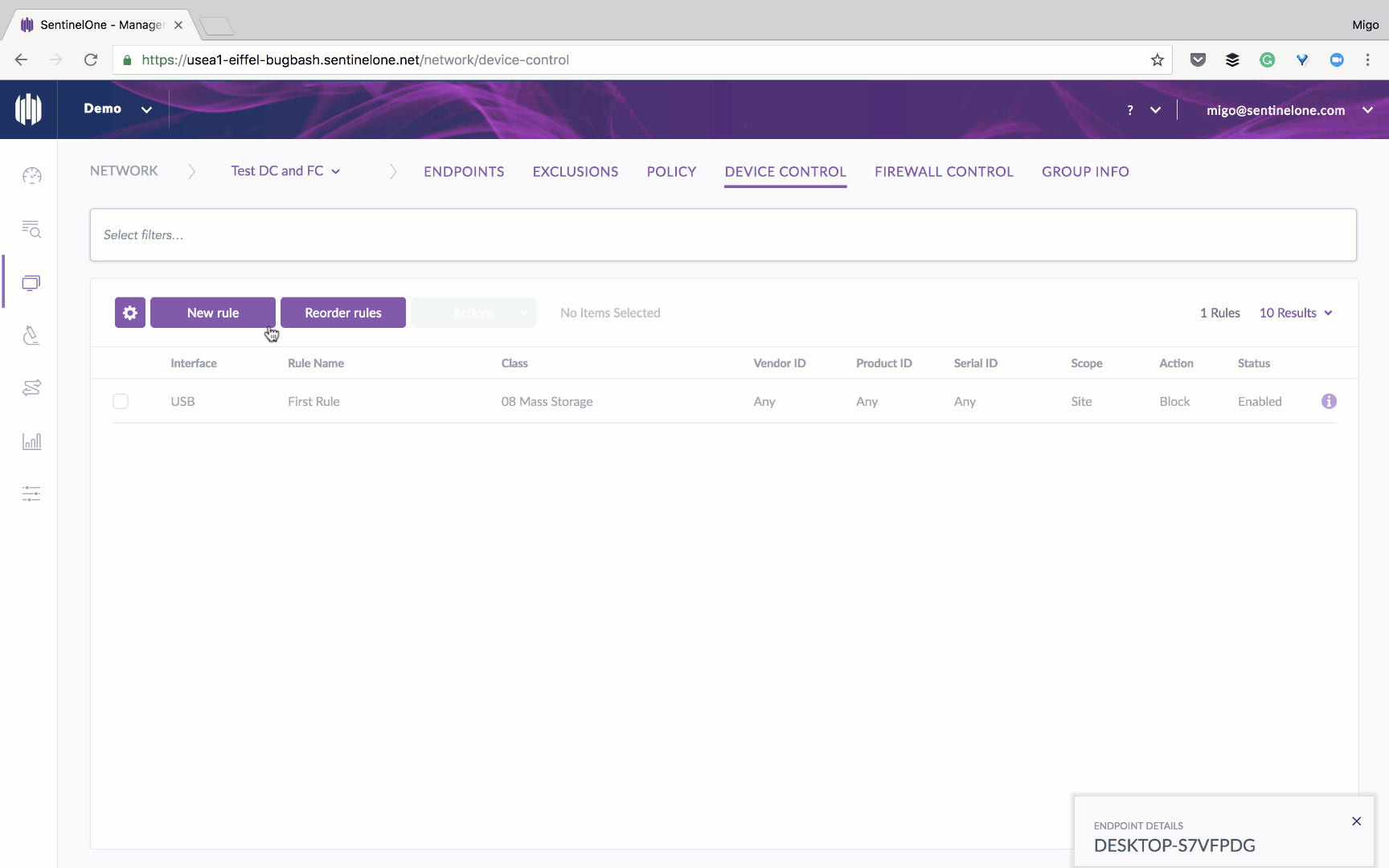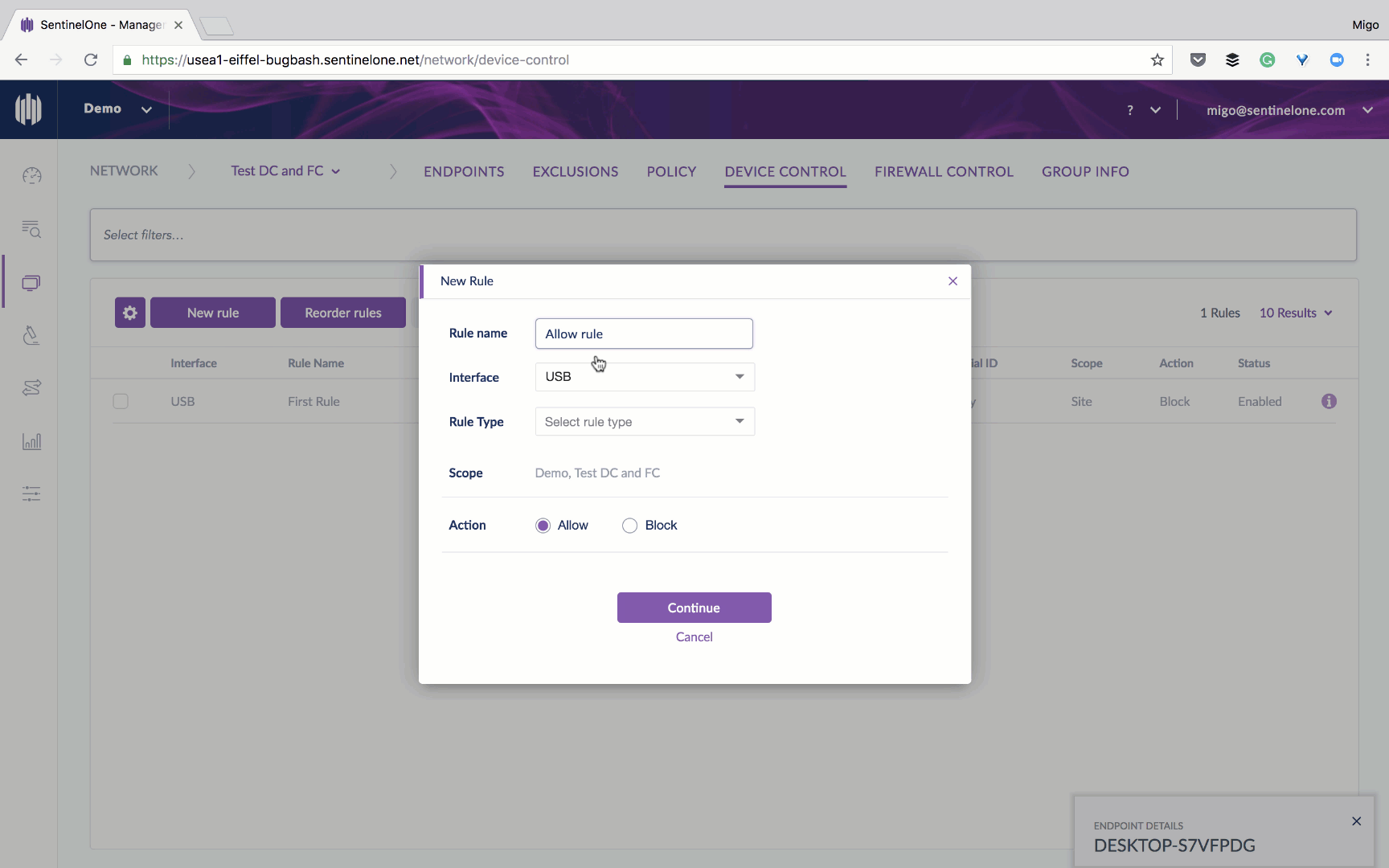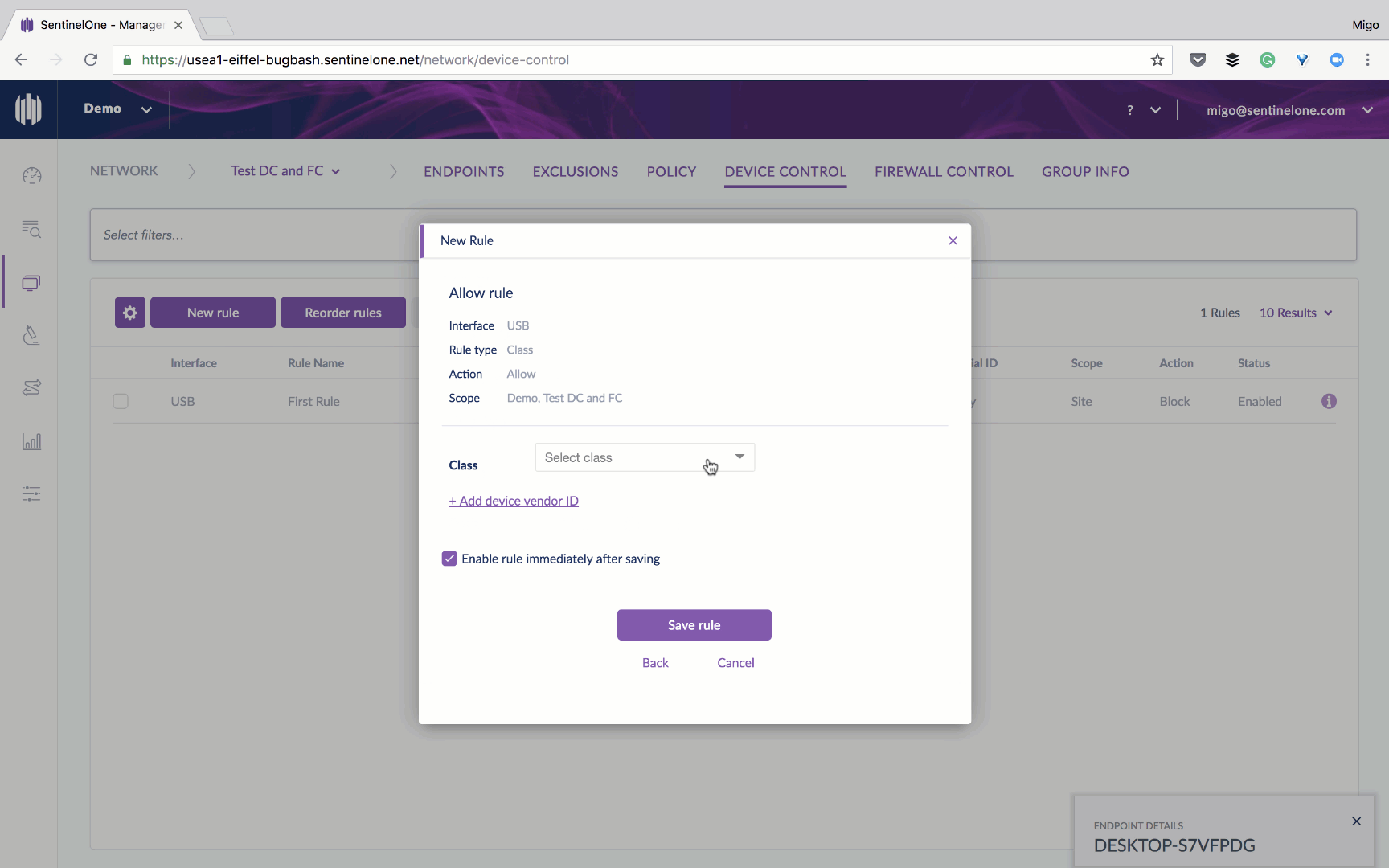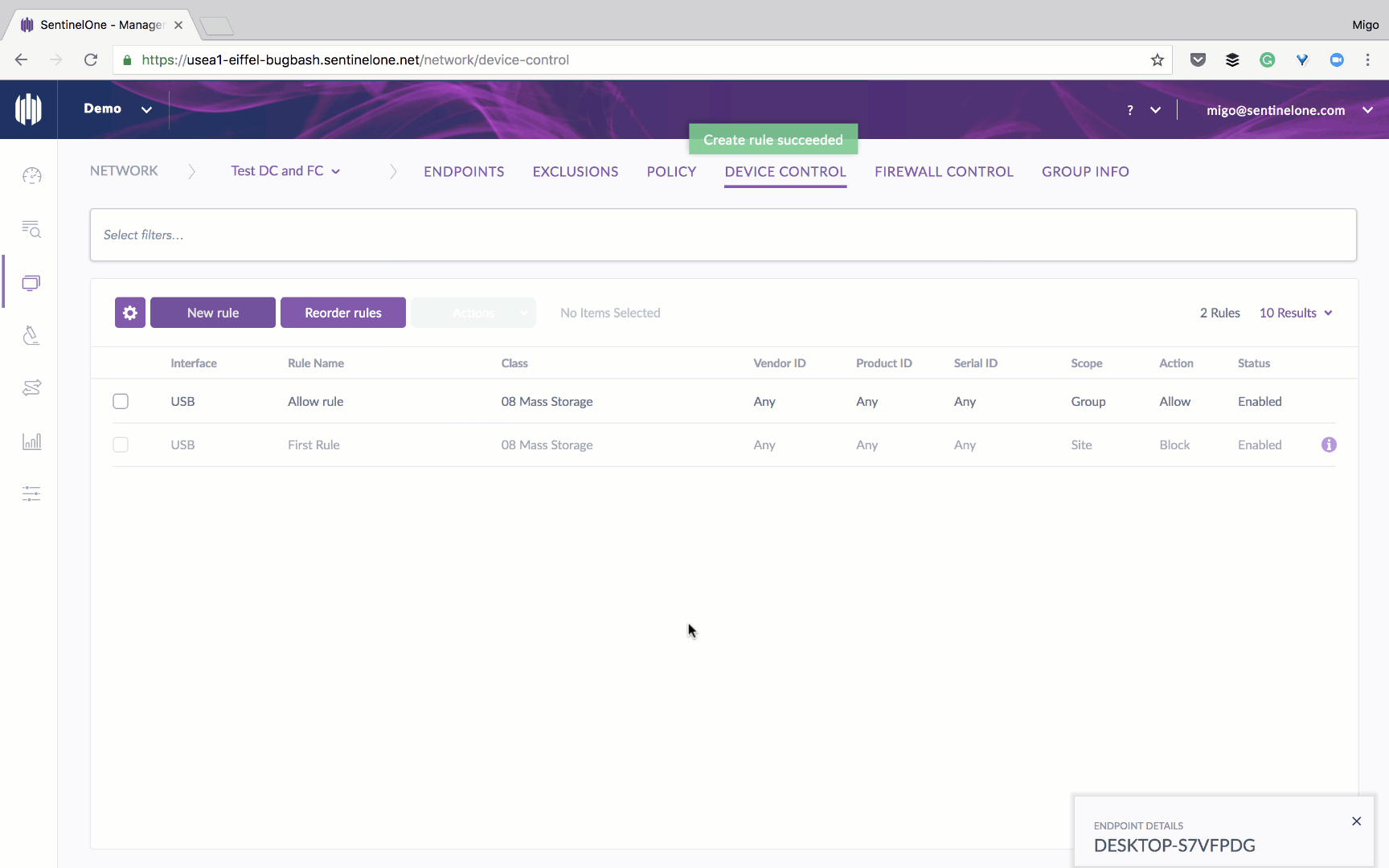
When we designed this capability, we wanted to make it easy and avoid the administrative overhead that is associated with access control. That’s why we took a granular approach, allowing you the level of control that best fits your needs. Device Control can be implemented at different levels, starting from a specific device ID, moving up to device family and going all the way up to device type. For a convenient quick-start, you can set a policy to monitor and log every usage of all peripheral devices, then create rules based on that.
To start, you can enable Device Control and set it to report both approved and blocked devices to activity logs.
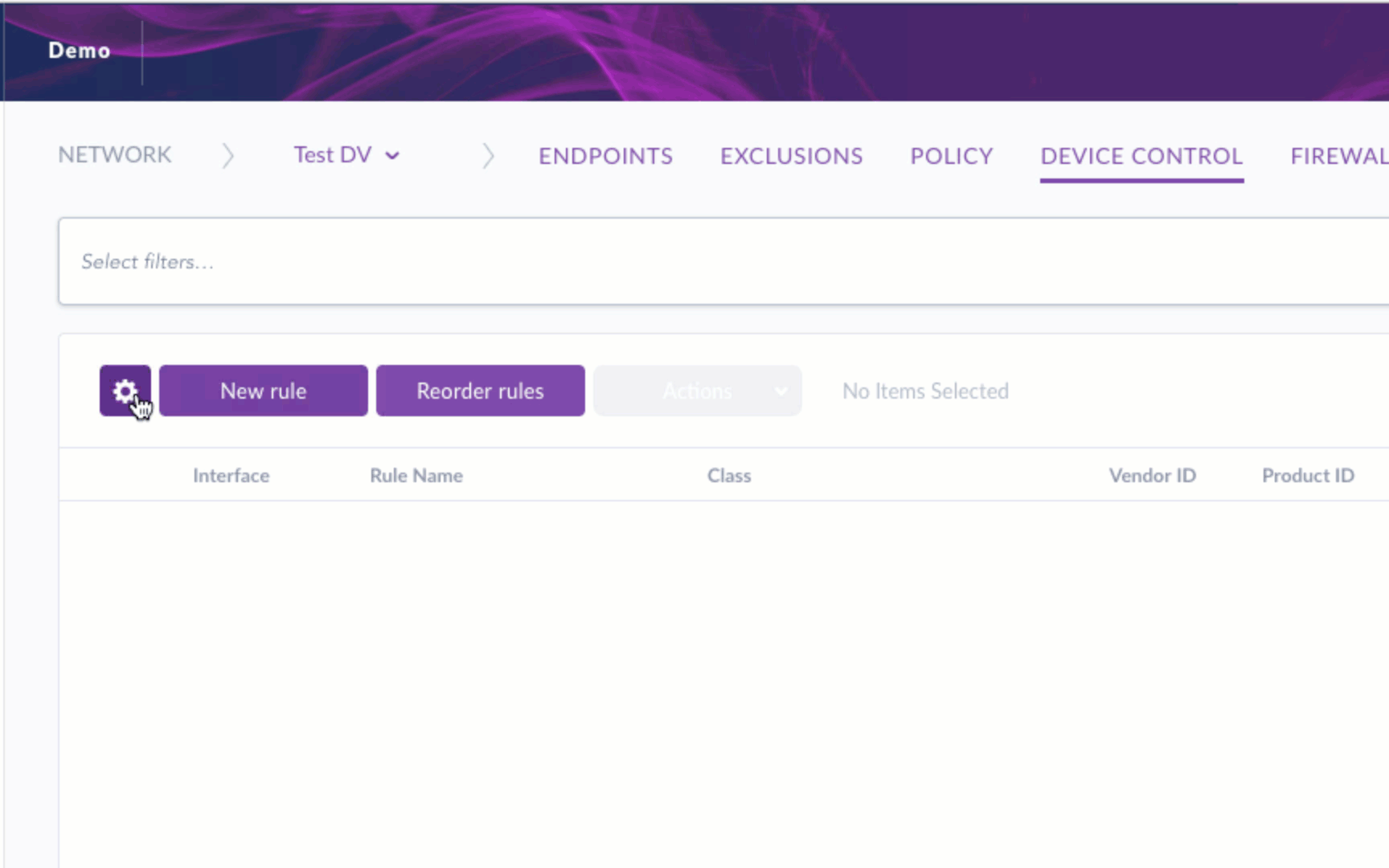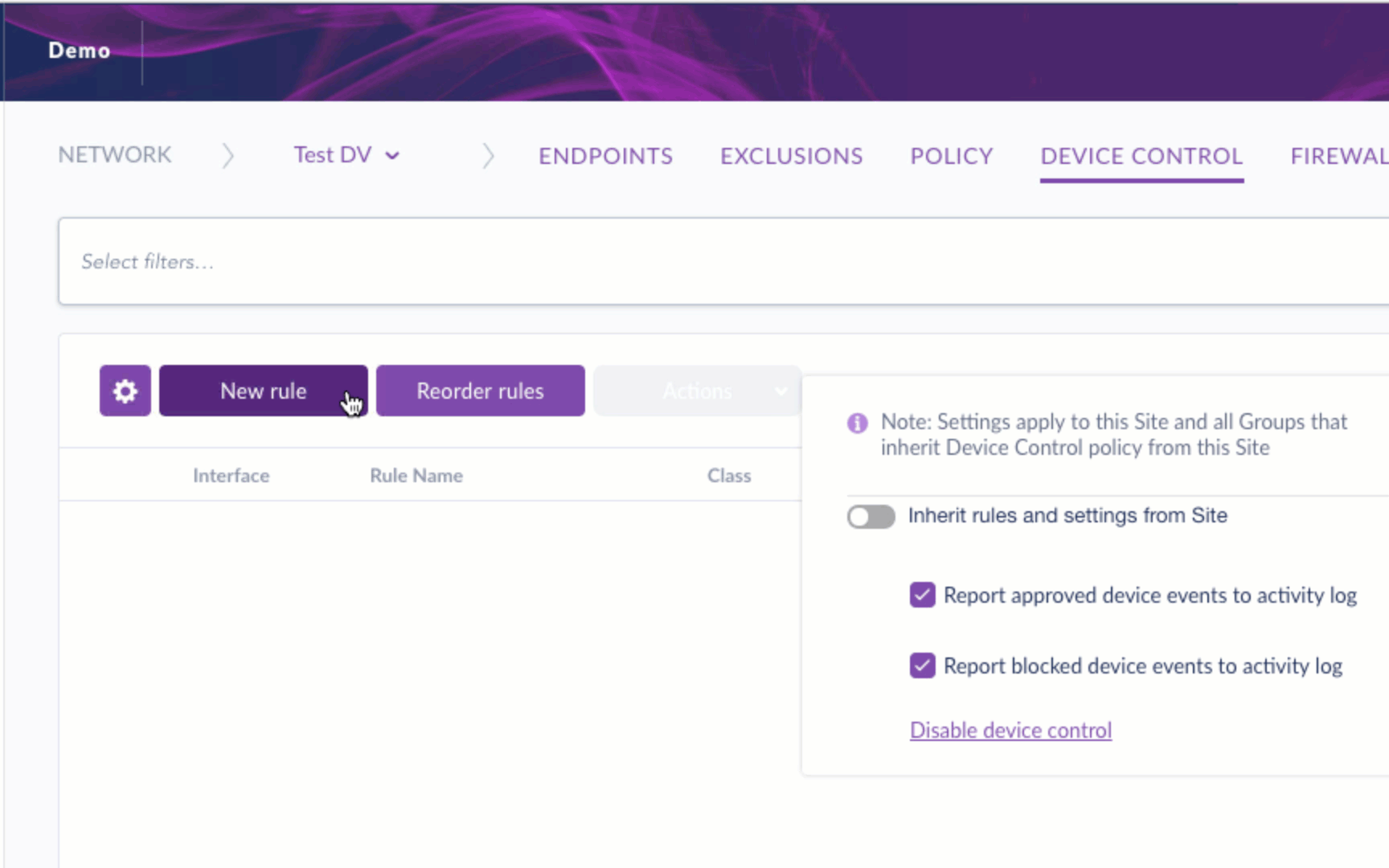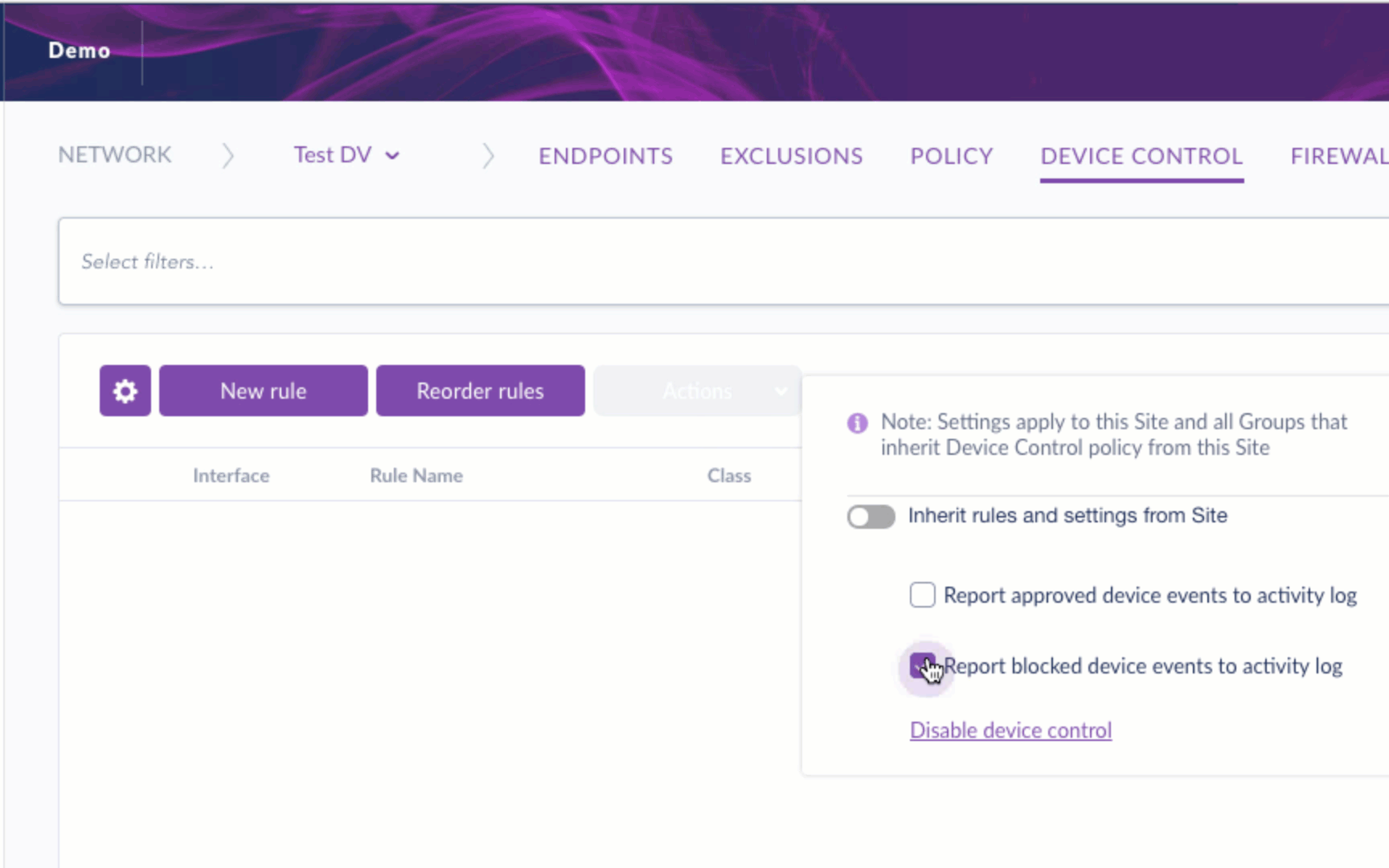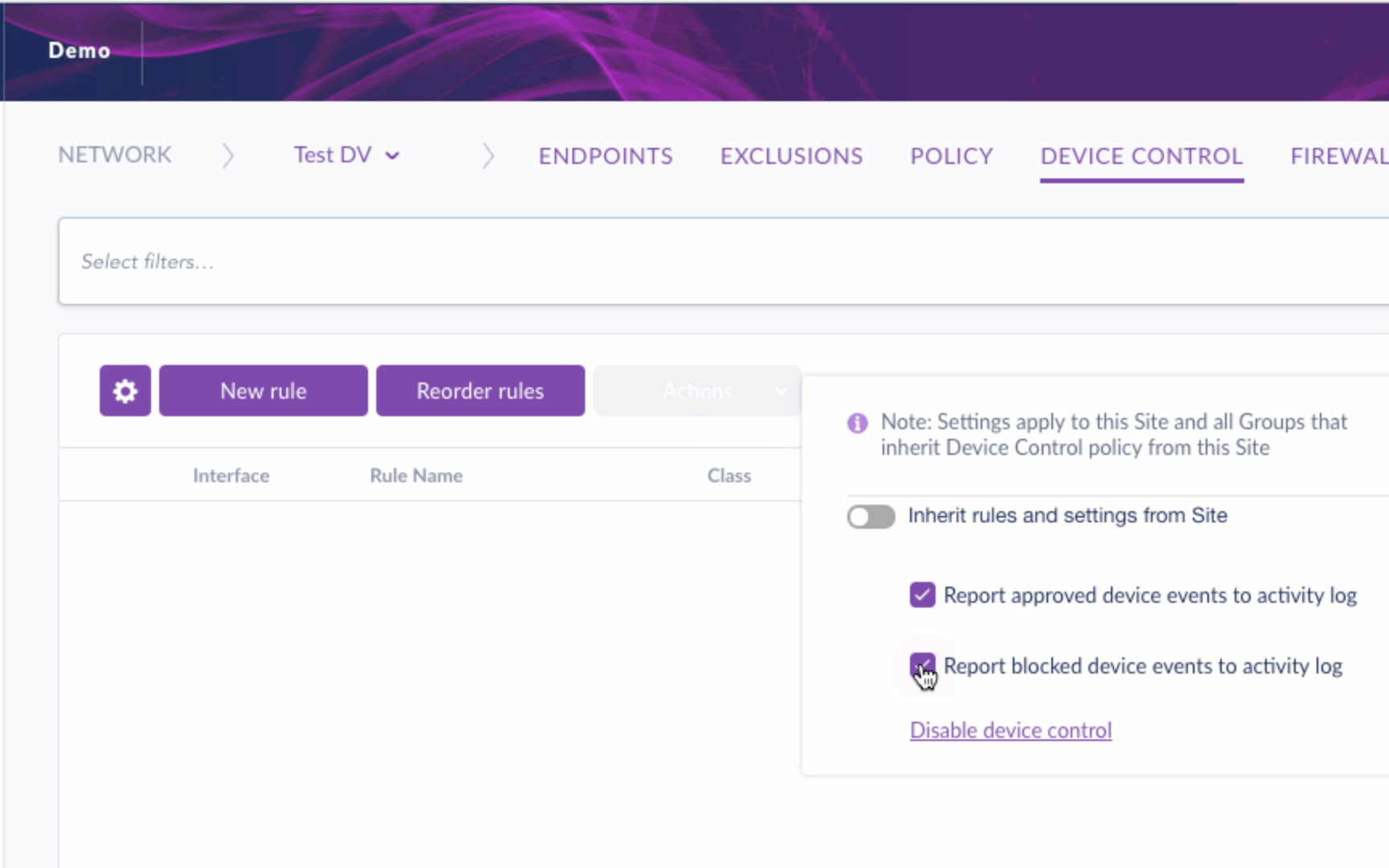
During initial implementation, IT administrators may choose a “monitor only” policy to ensure smooth integration before moving to the enforcement stage.
Demo
Conclusion
Together with SentinelOne Firewall Control feature, Device Control provides what some considered the missing pieces to fully replace legacy antivirus (AV) solutions with its next-gen product. Like other features of the platform, these are delivered via SentinelOne’s single agent, single codebase, single console architecture. As SentinelOne’s worldwide deployment grows, we continue to focus on solving the problems our customers care about. Device Control is available starting with Eiffel/2.8 agents.
