
ACCELERATE YOUR JOURNEY TO ZERO TRUST WITH APPGATE SDP
SOLUTION
CHECK APPGATE’S SOLUTIONS
Legacy network security solutions were not designed for today’s dynamic perimeter, resulting in vulnerabilities and complexity. Software-defined perimeter is a full-featured network security platform that incorporates the basic principles of Zero Trust.

Authenticate by identity, not IP address
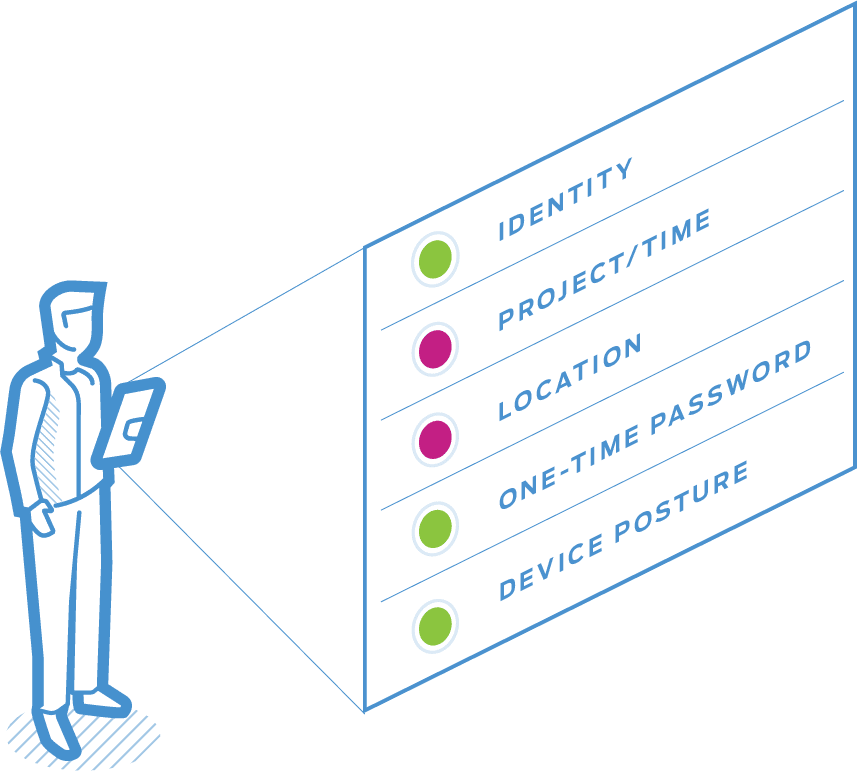
Create a multidimensional profile of an authorized user and device before granting access.
Dynamically adjust rights
As the context changes, rights dynamically adapt based on real-time policies and conditions.
Apply the principle of least privilege
Take advantage of microsegmentation to reduce the attack surface and eliminate lateral movement of all network resources.
Security
AppGate SDP up and running
A software-defined perimeter (SDP) architecture consists of three main components: a client, controller, and gateway. The controller is where the brains of the system reside, acting as a trusted intermediary for the system. The Controller checks the context and grants rights. The controller and the gateway are completely obfuscated.
APPGATE
- Using single packet authorization (SPA), the client device makes an access request and authenticates to the Controller. Controller evaluates credentials and applies access policies based on user, environment, and infrastructure.
- Controller checks context, passes live entitlement to Client. The Controller returns a cryptographically signed token back to the Client, which contains the authorized set of network resources.
- Using the SPA, the Client loads the live entitlements, which the Gateway uses to discover applications that match the user’s context. When the user attempts to access a resource-for example, by opening a web page on a protected server-the network driver forwards the token to the appropriate cloaked Gateway. The Gateway enforces additional policies in real time – network location, device attributes, time of day, and more. It can allow or deny access, or require an additional user action, such as requesting a disposable password.
- A dynamic segment of a network is created for this session. Once granted, all access to the resource travels from the Client through a secure, encrypted network tunnel and through the Gateway to the server. Access is logged by the LogServer, ensuring a permanent and auditable record of user access.
- The controller continuously monitors any context changes, adapts the segment of one accordingly.
Do you know what Zero Trust is?
Zero Trust is a paradigm shift toward a mindset of never trusting and checking extensively – whether you are a privileged user or not. Zero Trust takes a different approach to traditional security – never granting any kind of access, whether on a network or application layer – based on presumed trust. It requires trust to be earned through proactive device introspection, identity validation, and contextual analysis that is continually reassessed using a contextual risk-based approach.
